As a developer, performance optimization is an unavoidable topic that we will certainly encounter during daily development. Android performance optimization is actually quite mature, with mature routines, mature methodologies, mature open source frameworks, etc. For developers with less experience in performance optimization, there may be few opportunities to learn or summarize these mature routines, methodologies, or frameworks. So as a developer who has been doing performance optimization for many years, I will summarize some of the methodologies in this article for everyone's reference. The Essence of Performance Optimization First, let me introduce the essence of performance optimization. My understanding of its essence is: The essence of performance optimization is the reasonable and sufficient use of hardware resources to make the program perform better. And the purpose of the program performing better is to gain more retention, usage time, reputation, profit and other returns from customers. So based on the essence, the two most important things about performance optimization are: Reasonable and sufficient use of hardware resources Make the program perform better and gain returns Let's talk about these two things below. Reasonable and Sufficient Use of Hardware Resources Sufficient means making full use of the resources of the hardware, but sufficient is not necessarily reasonable. For example, we suddenly opened hundreds of threads at once, the CPU was fully utilized, but it was not reasonable. So reasonable means that the hardware resources exploited can have a positive effect on the performance of the program. Hardware resources include: CPU, memory, disk, battery, traffic (not a hardware resource, but also one of…
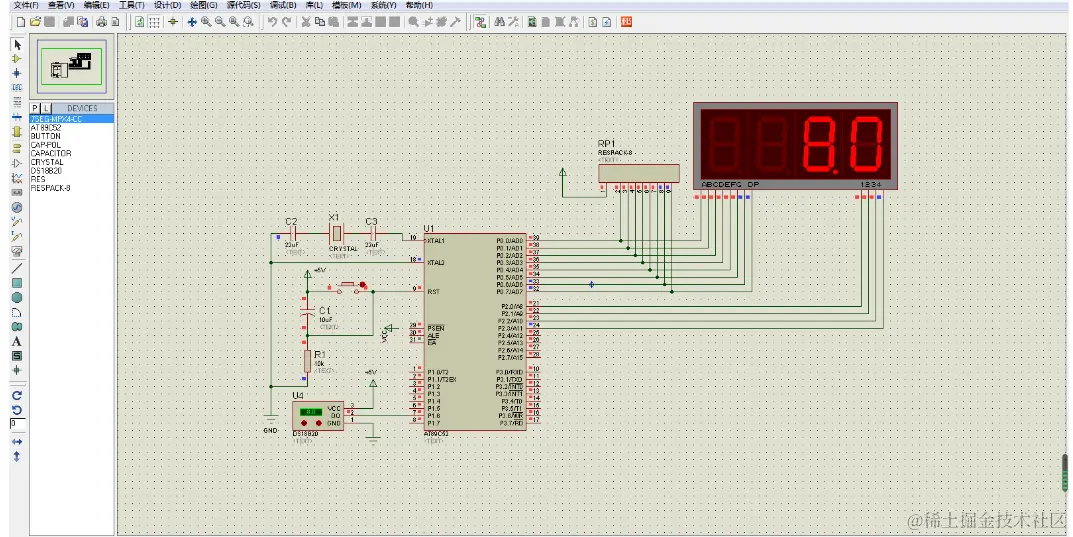
I. Project Introduction The digital thermometer is an electronic measuring instrument that is widely used in daily life and industrial fields to detect ambient temperature and convert it into a digital signal for display. With the development of modern science and technology, digital thermometers have gradually replaced traditional mercury thermometers and other methods, with advantages such as fast response, high precision, portability, etc. The digital thermometer designed based on 51 MCU is specifically applied to temperature detection in manufacturing, such as temperature controllers, oven temperature control, food processing, industrial furnaces and so on. The DS18B20 digital temperature sensor is used for temperature collection, the commonly used STC89C52 single-chip microcomputer control chip is used, and the 4-bit common anode digital tube is used to display the temperature data. When the set upper limit threshold is exceeded, the system will trigger the buzzer to alarm and prompt, thus ensuring accurate temperature control and safety. DS18B20 is a digital temperature sensor produced by Maxim Integrated. It uses a 1-Wire bus interface, which only needs one data line to simultaneously transmit data and power supply. Its main features are high precision, fast response speed, small size, and low price, and it is widely used in various temperature measurement occasions. The measurable temperature range of DS18B20 is -55°C to +125°C, with an accuracy of ±0.5°C (within the range of -10°C to +85°C). It integrates a temperature sensor, A/D converter and digital signal processing circuit inside, and can directly output digital temperature values. The working principle of DS18B20 is to use the effect of temperature on…
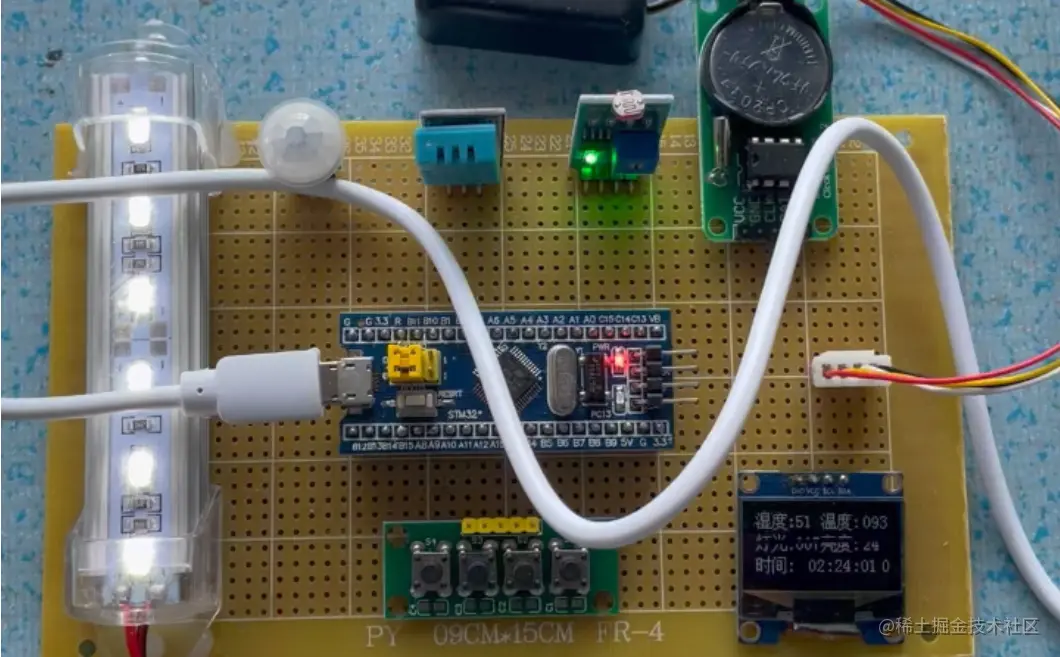
1. Project Background Intelligent home devices play an increasingly important role in modern life. As one of them, intelligent desk lamps have functions like adjusting brightness and color temperature to better meet people's needs for customized lighting environments. This article introduces the design of an intelligent desk lamp based on the STM32 microcontroller, which can adjust brightness and color temperature to provide users with a more comfortable experience. 2. Design Goals [1] Implement adjustable brightness and color temperature functions. [2] Add human body sensing module for automatic on/off. [3] Enable remote control of the lamp with a mobile phone. [4] Design simple, stable hardware circuits and user-friendly interfaces. 3. System Architecture 3.1 Hardware (1) MCU: STM32 series with rich peripherals and powerful processing capabilities. (2) Power supply: stable voltage regulator. (3) Light source: high-brightness LEDs with diffuser for even and soft lighting. (4) Human body sensing: infrared sensor to detect human presence and turn on light. (5) Wireless communication: WiFi/Bluetooth module for remote control with mobile app. 3.2 Software (1) Embedded software: Keil MDK, embedded C language programs for functions like brightness/color temperature control, human sensing, etc. (2) Mobile app: remote control of desk lamp functions. 3.3 Hardware Selection [1] MCU: STM32F103RCT6 [2] Light source: (1) High-brightness LEDs (2) Transparent lamp cover for even lighting [3] Human body sensing: (1) High sensitivity infrared sensor (2) Photoresistor for low light activation [4] Wireless module: HC05 Bluetooth module for communication with mobile device. 3.4 Hardware Design [1] MCU: STM32F103RCT6 [2] Infrared sensor: human presence detection [3] Photoresistor: ambient light intensity [4] LED:…
Before, the project used springcloud. The main components used were spring gateway, nacos, minio, load balancer, open-feign, etc. Then we deployed our microservices to virtual machines through docker. However, for security considerations, it needs to be migrated to Azure AKS (Kubernetes), so spring cloud needs to be reconstructed into spring boot. This way we don't need to maintain security policies for virtual machines ourselves, nor do we need to pay attention to patches. Combing project structure The project is organized into microservices. There are about 5 business services and 4 public services. The main reconstruction is concentrated in gateway and auth. The reconstruction of public packages is less, mainly changing open-feign access to call by url instead of by service name as before. In Kubernetes, we use Traefik2 to replace the gateway function. If you don't know Traefik2, you can check out my previous articles. At the same time, an authorization interface needs to be provided for authorization, used with Traefik2, so that each request will be authenticated. Start reconstruction Determine branch First of all, we definitely pull a new branch for these changes, even if it doesn't work well, it won't affect others. So let's call the branch name feature/AKS-migrate. Reconstruct gateway First, comment out unnecessary dependency packages in the pom file, such as spring cloud gateway, nacos, sentinel and other spring cloud related components. After commenting out, check what errors there are in the code and modify them accordingly. There are quite a few gateway filters and handlers used in our project. At first I thought that since…
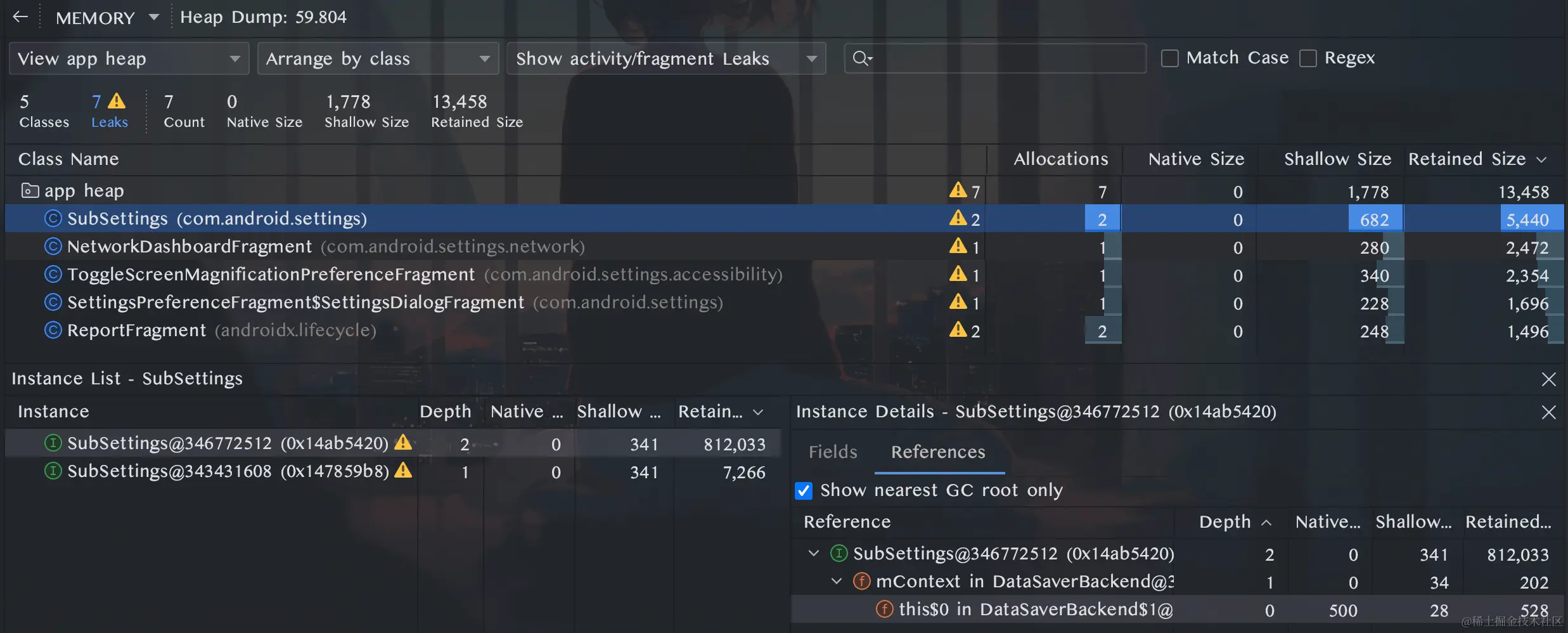
Analysis Idea Memory leak refers to the phenomenon where some objects are no longer in use in the Android process, but are referenced by some longer-lived objects, causing the occupied memory resources to fail to be recycled by GC, and memory usage continues to increase. Memory leaks are a common factor leading to decreased performance and lag in our applications. The core ideas for solving such problems can be summarized in two steps: Simulate memory leak operations, observe changes in the application Heap memory, and determine the approximate location of the problem; Expand the analysis for the specific location, find the complete reference chain from the leaked object to the GC Root, and fix the memory leak from the source. Analysis Tool: Android Studio Profiler The commonly used memory analysis tools in Profiler are two: Memory Chart and Heap Dump. The memory curve can observe the memory usage status in real time to assist us in performing dynamic memory analysis. A typical phenomenon of memory leaks in the memory curve is a ladder-like shape. Once it rises, it becomes difficult to decrease. For example, after an Activity leak, repeatedly opening and closing the page, the memory usage will keep rising, and after clicking the trash can icon to manually GC, the usage cannot decrease to the level before opening the Activity. At this point, it is highly likely that a memory leak has occurred. At this time, we can manually dump the memory distribution in the application heap at that moment for static analysis: UI indicator descriptions: Allocations: Number of…
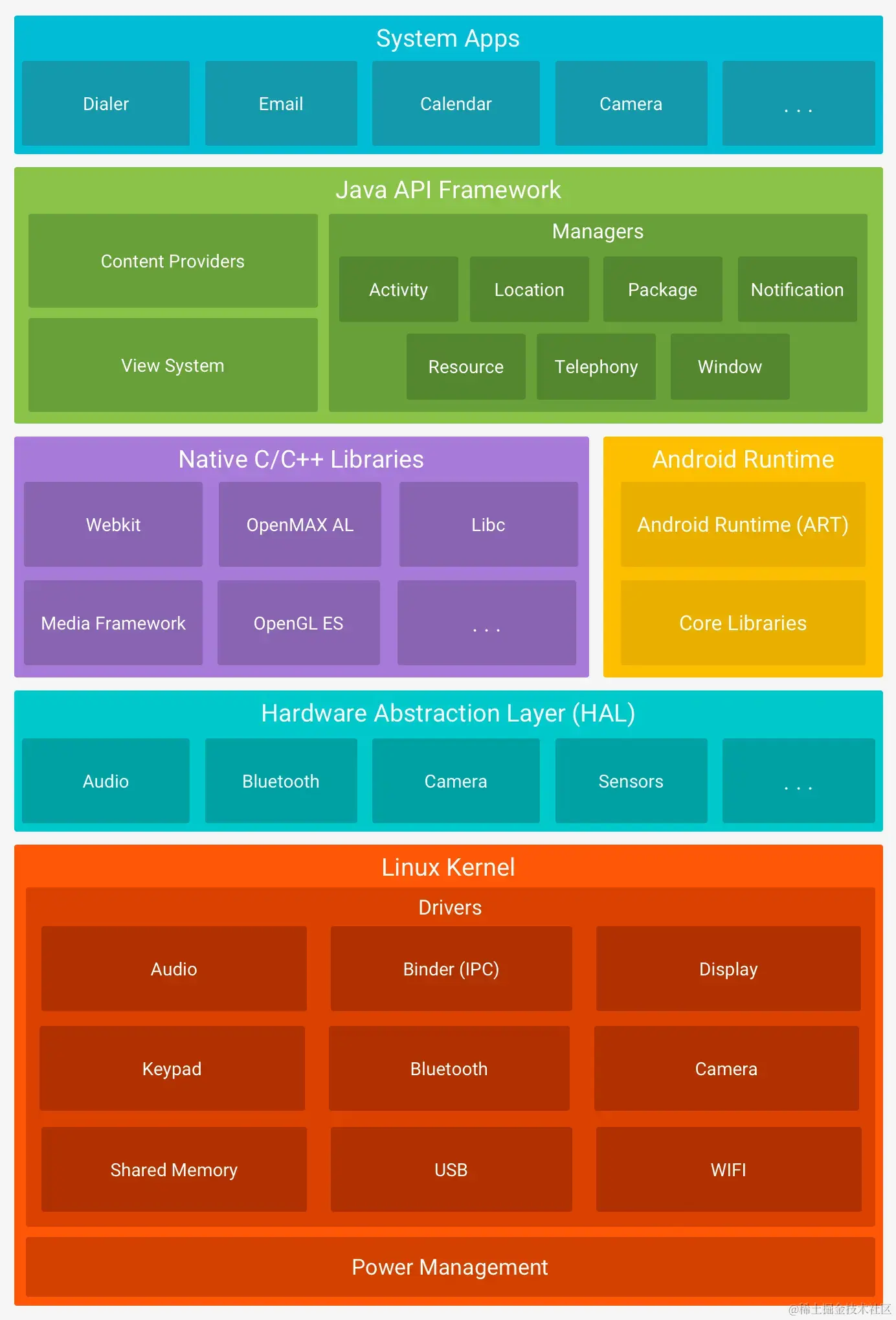
The figure above is the overall architecture of Android. Android Runtime is to Android what the heart is to the human body. It is the environment where Android programs are loaded and run. This article mainly focuses on the Android Runtime part and explores the development and current status of Android Runtime. It also introduces the feasibility of using Profile-Guided Optimization (PGO) technology to optimize application launch speed. Evolution of App Runtime JVM Native Android code is written in Java or Kotlin and compiled into .class files by javac or kotlinc. Before Android, these .class files would be input into the JVM for execution. The JVM can be simply divided into three subsystems: Class Loader, Runtime Data Area, and Execution Engine. Among them, the Class Loader is mainly responsible for loading classes, verifying bytecode, linking symbol references, allocating memory for static variables and static methods, and initializing them. Runtime Data is responsible for storing data, divided into method area, heap area, stack area, program counter, and native method stack. The Execution Engine is responsible for executing binary code and garbage collection. In the Execution Engine, Interpreter or JIT execution is used. Interpreter means interpreting the binary code during execution. Interpreting the same binary code each time is wasteful, so hot binary code will be JIT compiled into machine code for faster execution later. DVM (Android 2.1/2.2) JVM is a stack-based runtime environment. Mobile devices have higher requirements for performance and storage space, so Android uses the register-based Dalvik VM. To convert from JVM to DVM, we need to convert .class…
Summary: How to slim down APKs is an important optimization technique for Android. Both installation and updating of APKs require network downloading to devices, and the smaller the APK, the better the user experience. Through detailed analysis of the internal mechanisms of APKs, the author provides optimization methods and techniques for each component of APKs, and implements a minimization process for a basic APK. Body: In golf, the player with the lowest score wins. Let's apply this principle to Android app development. We will play with an APK called "ApkGolf", with the goal of creating an app with the smallest number of bytes possible that can be installed on a device running Oreo. Baseline Measurement To start, we generate a default app using Android Studio, create a keystore, and sign the app. We then use the command stat -f%z $filename to measure the number of bytes of the generated APK file. Furthermore, to ensure the APK works properly, we install it on a Nexus 5x phone running Oreo. Looks good. But now our APK size is close to 1.5Mb. APK Analyser Considering our app's functionality is very simple, the 1.5Mb size seems bloated. So let's dig into the project to see if there are any obvious areas we can trim to immediately reduce the file size. Android Studio generated: A MainActivity extending AppCompatActivity; A layout file using ConstraintLayout as the root view; Value files containing three colors, one string resource, and one theme; AppCompat and ConstraintLayout support libraries; An AndroidManifest.xml file; PNG format launcher icons, square, round, and foreground. The…
Preface The origin of diff algorithms The diff algorithm is a method used to compare differences between two text files. It helps developers and other tech professionals compare and modify text files. The diff algorithm was originally published by Gene Myers in 1986. The basic idea is to find the shortest edit script between two files to convert one file into the other. Application context of diff algorithms Diff algorithms are mainly used in areas like code version control systems, file comparison tools, and database version control. With the rapid development of software engineering, the scale and complexity of code is increasing. The application of diff algorithms is becoming more and more important. Different diff algorithms have their own advantages and disadvantages in different application scenarios. Therefore, more differential algorithms need to be developed to meet the requirements of different scenarios. Traditional diff algorithms Longest Common Subsequence (LCS) algorithm The Longest Common Subsequence (LCS) algorithm is a classic algorithm for comparing the similarity between two sequences. It is also a type of diff algorithm. This algorithm compares the same parts of two text sequences and marks the different parts. The basic principle of the LCS algorithm is to find the longest common subsequence between two sequences and find differences within it. Here is a sample Python implementation of the LCS algorithm: def LCS(X, Y): m = len(X) n = len(Y) # Initialization L = [[0] * (n+1) for i in range(m+1)] for i in range(m+1): for j in range(n+1): if i == 0 or j == 0: L[i][j] = 0…
Hi everyone👋🏻, I want to share with you all how to build Android apps using the latest trends in 2023. What is Android? Android is an open source operating system based on the Linux kernel, developed by Google. It is widely used on a variety of devices including smartphones, tablets, TVs and smartwatches. Currently, Android is the most used mobile operating system in the world; according to statcounter, with the past 12 months as a sample, Android has a market share of 70.77%. Next, I will mention a list of tools, libraries, architectures, guidelines and other utilities that I think are very important for building modern apps on Android. Kotlin ❤️ Kotlin is a programming language developed by JetBrains. Recommended by Google, it was officially announced in May 2017 (see the publication here). It is a modern programming language with compatibility with Java that can run on the JVM, which has made its adoption very fast in Android application development. Whether you are new to Android or not, you should consider having Kotlin as your first choice, don't swim against the tide 🏊🏻😎, Google announced this in Google I/O 2019. With Kotlin you will be able to use all the features of a modern language including the powerful Coroutines and using modern libraries developed for the Android ecosystem. The official Kotlin documentation is here Jetpack Compose 😍 Jetpack Compose is the modern toolkit recommended by Android for building native UI. It simplifies and accelerates UI development on Android. Jetpack Compose documentation Jetpack Compose is part of the Android Jetpack libraries,…
Today let's take an in-depth look at SSL, TLS and mTLS and other important communication security protocols. Although from a holistic systems design perspective, this topic may not be mission critical, it is still worth our time to understand it thoroughly. 1. SSL Protocol SSL, or Secure Socket Layer, is a protocol that aims to encrypt and secure the safety of internet communications. Although it first emerged in 1995, it has since been replaced by the later Transport Layer Security (TLS) protocol. The advent of SSL marked a focus on security for internet communications. In the early days, data on networks was transmitted in plaintext, making sensitive information vulnerable to eavesdropping and tampering. SSL effectively solved this problem by introducing strong data encryption and authentication mechanisms, providing robust protection for user privacy and data integrity. 2. Why Still Called SSL Certificates? Although SSL is deprecated, most major certificate authorities still refer to their certificates as SSL certificates. This is due to legacy conventions around naming that still persist. Also, many sites and systems still use SSL certificates, so the naming convention still has practical meaning. 3. The Importance of SSL The importance of SSL cannot be understated. Its advent completely changed the security paradigm for internet communications, fundamentally enhancing the security of data transmission. On the internet, data can travel between thousands of nodes, and SSL ensures it is difficult to steal or tamper with by encrypting the data stream. This security provided a solid foundation for online banking, e-commerce, and various other online applications. 4. Transport Layer Security (TLS)…